Remove Brontok Virus Urself
POWER OF BRONTOK:- it will hide ur folder options ......it will disable ur registry edit and task manager......etc...
its the most sticky virus ..
u can Remove it
be an ethical Hacker
It works~~!!
Start ur computer in safe mode with command prompt and type the followinf command to enable registry editor:-
reg delete HKCU\software\microsoft\windows\currentversion\policies\system /v "DisableRegistryTools"
and run HKLM\software\microsoft\windows\currentversion\policies\system /v "DisableRegistryTools"
after this ur registry editor is enable
type explorer
go to run and type regedit
then follow the following path :-
HKLM\Software\Microsoft\Windows\Currentversion\Run
on the right side delete the entries which contain 'Brontok' and 'Tok-' words.
after that restart ur system
open registry editor and follow the path to enable folder option in tools menu
HKCU\Software\Microsoft\Windows\Currentversion\Policies\Explorer\ 'NoFolderOption'
delete this entry and restart ur computer
and search *.exe files in all drives (search in hidden files also)
remove all files which are display likes as folder icon.
ur computer is completely free from virus brontok
src="http://pagead2.googlesyndication.com/pagead/show_ads.js">
Monday, May 05, 2008 | 0 Comments
Search passwords and Juicy Info : Digg Google
Introduction
This is not about finding sensitive data during an assessment as much as
it is about what the “bad guys” might do to troll for the data.The examples presented
generally represent the lowest-hanging fruit on the security
tree. Hackers target this information on a daily basis.To protect against this type
of attacker, we need to be fairly candid about the worst-case possibilities.We
won’t be overly candid, however.
We start by looking at some queries that can be used to uncover usernames,
the less important half of most authentication systems.The value of a username is
often overlooked, but, an entire multimilliondollar
security system can be shattered through skillful crafting of even the
smallest, most innocuous bit of information.
Next, we take a look at queries that are designed to uncover passwords. Some
of the queries we look at reveal encrypted or encoded passwords, which will take
a bit of work on the part of an attacker to use to his or her advantage.We also
take a look at queries that can uncover cleartext passwords.These queries are some
of the most dangerous in the hands of even the most novice attacker. What could
make an attack easier than handing a username and cleartext password to an
attacker?
We wrap up by discussing the very real possibility of uncovering
highly sensitive data such as credit card information and information used to
commit identity theft, such as Social Security numbers. Our goal here is to
explore ways of protecting against this very real threat.To that end, we don’t go
into details about uncovering financial information and the like. If you’re a “dark
side” hacker, you’ll need to figure these things out on your own.
Searching for Usernames
Most authentication mechanisms use a username and password to protect information.
To get through the “front door” of this type of protection, you’ll need to
determine usernames as well as passwords. Usernames also can be used for social
engineering efforts, as we discussed earlier.
Many methods can be used to determine usernames. In Chapter 10, we
explored ways of gathering usernames via database error messages. In Chapter 8
we explored Web server and application error messages that can reveal various
information, including usernames.These indirect methods of locating usernames
are helpful, but an attacker could target a usernames directory
query like “your username is”. This phrase can locate help pages that describe the
username creation process,
information gleaned from other sources, such as Google Groups posts or phone
listings.The usernames could then be recycled into various other phases of the
attack, such as a worm-based spam campaign or a social-engineering attempt.An
attacker can gather usernames from a variety of sources, as shown in the sample
queries listed
Sample Queries That Locate Usernames
Query Description
inurl:admin inurl:userlist Generic userlist files
inurl:admin filetype:asp Generic userlist files
inurl:userlist
inurl:php inurl:hlstats intext: Half-life statistics file, lists username and
Server Username other information
filetype:ctl inurl:haccess. Microsoft FrontPage equivalent of htaccess
ctl Basic shows Web user credentials
Query Description
filetype:reg reg intext: Microsoft Internet Account Manager can
”internet account manager” reveal usernames and more
filetype:wab wab Microsoft Outlook Express Mail address
books
filetype:mdb inurl:profiles Microsoft Access databases containing (user)
profiles.
index.of perform.ini mIRC IRC ini file can list IRC usernames and
other information
inurl:root.asp?acs=anon Outlook Mail Web Access directory can be
used to discover usernames
filetype:conf inurl:proftpd. PROFTP FTP server configuration file reveals
conf –sample username and server information
filetype:log username putty PUTTY SSH client logs can reveal usernames
and server information
filetype:rdp rdp Remote Desktop Connection files reveal user
credentials
intitle:index.of .bash_history UNIX bash shell history reveals commands
typed at a bash command prompt; usernames
are often typed as argument strings
intitle:index.of .sh_history UNIX shell history reveals commands typed at
a shell command prompt; usernames are
often typed as argument strings
“index of ” lck Various lock files list the user currently using
a file
+intext:webalizer +intext: Webalizer Web statistics page lists Web user-
Total Usernames +intext: names and statistical information
”Usage Statistics for”
filetype:reg reg HKEY_ Windows Registry exports can reveal
CURRENT_USER username usernames and other information
Underground Googling
Searching for a Known Filename
Remember that there are several ways to search for a known filename.
One way relies on locating the file in a directory listing, like intitle:index.of
install.log. Another, often better, method relies on the filetype operator,
as in filetype:log inurl:install.log. Directory listings are not all that
common. Google will crawl a link to a file in a directory listing, meaning
that the filetype method will find both directory listing entries as well as
files crawled in other ways.
In some cases, usernames can be gathered from Web-based statistical programs
that check Web activity.The Webalizer program shows all sorts of information
about a Web server’s usage. Output files for the Webalizer program can be
located with a query such as intext:webalizer intext:”Total Usernames” intext:”Usage
Statistics for”. Among the information displayed is the username that was used to
connect to the Web server, as shown in Figure 9.2. In some cases, however, the
usernames displayed are not valid or current, but the “Visits” column lists the
number of times a user account was used during the capture period.This enables
an attacker to easily determine which accounts are more likely to be valid.
The Windows registry holds all sorts of authentication information, including
usernames and passwords.Though it is unlikely (and fairly uncommon) to locate
live, exported Windows registry files on the Web, at the time of this writing
there are nearly 100 hits on the query filetype:reg HKEY_CURRENT_USER
username, which locates Windows registry files that contain the word username
and in some cases passwords,
As any talented attacker or security person will tell you, it’s rare to get information
served to you on a silver platter. Most decent finds take a bit of persistence,
creativity, intelligence, and just a bit of good luck. For example, consider
the Microsoft Outlook Web Access portal, which can be located with a query
like inurl:root.asp?acs=anon. At the time of this writing, fewer than 50 sites are
returned by this query, even though there a certainly more than 50 sites running
the Microsoft Web-based mail portal. Regardless of how you might locate a site
running this e-mail gateway, it’s not uncommon for the site to host a public
directory (denoted “Find Names,” by default)
The public directory allows access to a search page that can be used to find
users by name. In most cases, wildcard searching is not allowed, meaning that a
search for * will not return a list of all users, as might be expected. Entering a
search for a space is an interesting idea, since most user descriptions contain a
space, but most large directories will return the error message “This query would
return too many addresses!” Applying a bit of creativity, an attacker could begin
searching for individual common letters, such as the “Wheel of Fortune letters”
R, S,T, L, N, and E. Eventually one of these searches will most likely reveal a list
of user information like
Once a list of user information is returned, the attacker can then recycle the
search with words contained in the user list, searching for the words Voyager,
Freshmen, or Campus, for example.Those results can then be recycled, eventually
resulting in a nearly complete list of user information.
Searching for Passwords
Password data, one of the “Holy Grails” during a penetration test, should be protected.
Unfortunately, many examples of Google queries can be used to locate
passwords on the Web, as shown in Table 9.2.
Table 9.2 Queries That Locate Password Information
Query Description
inurl:/db/main.mdb ASP-Nuke passwords
filetype:cfm “cfapplication ColdFusion source with potential passwords
name” password
filetype:pass pass intext:userid dbman credentials
allinurl:auth_user_file.txt DCForum user passwords
eggdrop filetype:user user Eggdrop IRC user credentials
filetype:ini inurl:flashFXP.ini FlashFXP FTP credentials
filetype:url +inurl:”ftp://” FTP bookmarks cleartext passwords
+inurl:”@”
inurl:zebra.conf intext: GNU Zebra passwords
password -sample -test
-tutorial –download
filetype:htpasswd htpasswd HTTP htpasswd Web user credentials
intitle:”Index of” “.htpasswd” HTTP htpasswd Web user credentials
“htgroup” -intitle:”dist”
-apache -htpasswd.c
intitle:”Index of” “.htpasswd” HTTP htpasswd Web user credentials
htpasswd.bak
“http://*:*@www” bob:bob HTTP passwords (bob is a sample username)
“sets mode: +k” IRC channel keys (passwords)
“Your password is * Remember IRC NickServ registration passwords
this for later use”
signin filetype:url JavaScript authentication credentials
Queries That Locate Password Information
Query Description
LeapFTP intitle:”index.of./” LeapFTP client login credentials
sites.ini modified
inurl:lilo.conf filetype:conf LILO passwords
password -tatercounter2000
-bootpwd –man
filetype:config config intext: Microsoft .NET application credentials
appSettings “User ID”
filetype:pwd service Microsoft FrontPage Service Web passwords
intitle:index.of Microsoft FrontPage Web credentials
administrators.pwd
“# -FrontPage-” inurl:service.pwd Microsoft FrontPage Web passwords
ext:pwd inurl:_vti_pvt inurl: Microsoft FrontPage Web passwords
(Service | authors | administrators)
inurl:perform filetype:ini mIRC nickserv credentials
intitle:”index of” intext: mySQL database credentials
connect.inc
intitle:”index of” intext: mySQL database credentials
globals.inc
filetype:conf oekakibbs Oekakibss user passwords
filetype:dat wand.dat Opera‚ ÄúMagic Wand‚Äù Web credentials
inurl:ospfd.conf intext: OSPF Daemon Passwords
password -sample -test
-tutorial –download
index.of passlist Passlist user credentials
inurl:passlist.txt passlist.txt file user credentials
filetype:dat “password.dat” password.dat files
inurl:password.log filetype:log password.log file reveals usernames, passwords,
and hostnames
filetype:log inurl:”password.log” password.log files cleartext passwords
inurl:people.lst filetype:lst People.lst generic password file
intitle:index.of config.php PHP Configuration File database credentials
inurl:config.php dbuname dbpass PHP Configuration File database credentials
inurl:nuke filetype:sql PHP-Nuke credentials
Queries That Locate Password Information
Query Description
filetype:conf inurl:psybnc.conf psyBNC IRC user credentials
“USER.PASS=”
filetype:ini ServUDaemon servU FTP Daemon credentials
filetype:conf slapd.conf slapd configuration files root password
inurl:”slapd.conf” intext: slapd LDAP credentials
”credentials” -manpage
-”Manual Page” -man: -sample
inurl:”slapd.conf” intext: slapd LDAP root password
”rootpw” -manpage
-”Manual Page” -man: -sample
filetype:sql “IDENTIFIED BY” –cvs SQL passwords
filetype:sql password SQL passwords
filetype:ini wcx_ftp Total Commander FTP passwords
filetype:netrc password UNIX .netrc user credentials
index.of.etc UNIX /etc directories contain various credential
files
intitle:”Index of..etc” passwd UNIX /etc/passwd user credentials
intitle:index.of passwd UNIX /etc/passwd user credentials
passwd.bak
intitle:”Index of” pwd.db UNIX /etc/pwd.db credentials
intitle:Index.of etc shadow UNIX /etc/shadow user credentials
intitle:index.of master.passwd UNIX master.passwd user credentials
intitle:”Index of” spwd.db UNIX spwd.db credentials
passwd -pam.conf
filetype:bak inurl:”htaccess| UNIX various password file backups
passwd|shadow|htusers
filetype:inc dbconn Various database credentials
filetype:inc intext:mysql_ Various database credentials, server names
connect
filetype:properties inurl:db Various database credentials, server names
intext:password
inurl:vtund.conf intext:pass –cvs Virtual Tunnel Daemon passwords
inurl:”wvdial.conf” intext: wdial dialup user credentials
Queries That Locate Password Information
Query Description
filetype:mdb wwforum Web Wiz Forums Web credentials
“AutoCreate=TRUE password=*”Website Access Analyzer user passwords
filetype:pwl pwl Windows Password List user credentials
filetype:reg reg +intext: Windows Registry Keys containing user
”defaultusername” intext: credentials
”defaultpassword”
filetype:reg reg +intext: Windows Registry Keys containing user
”internet account manager” credentials
“index of/” “ws_ftp.ini” WS_FTP FTP credentials
“parent directory”
filetype:ini ws_ftp pwd WS_FTP FTP user credentials
inurl:/wwwboard wwwboard user credentials
In most cases, passwords discovered on the Web are either encrypted or
encoded in some way. In most cases, these passwords can be fed into a password
cracker such as John the Ripper from www.openwall.com/john to produce
plaintext passwords that can be used in an attack. Figure 9.6 shows the results of
the search ext:pwd inurl:_vti_pvt inurl:(Service | authors | administrators), which
combines a search for some common
Exported Windows registry files often contain encrypted or encoded passwords
as well. If a user exports the Windows registry to a file and Google subsequently
crawls that file, a query like filetype:reg intext:”internet account manager”
could reveal interesting keys containing password data
ress. Note that live, exported Windows registry files are not very common, but it’s
not uncommon for an attacker to target a site simply because of one exceptionally
insecure file. It’s also possible for a Google query to uncover cleartext passwords.
These passwords can be used as is without having to employ a
password-cracking utility. In these extreme cases, the only challenge is determining
the username as well as the host on which the password can be used. As
shown in Figure 9.8, certain queries will locate all the following information:
usernames, cleartext passwords, and the host that uses that authentication!
There is no magic query for locating passwords, but during an assessment,
remember that the simplest queries directed at a site can have amazing results, as
we discussed in , Chapter 7, Ten Simple Searches. For example, a query like “Your
password” forgot would locate pages that provide a forgotten password recovery
mechanism.The information from this type of query can be used to formulate
any of a number of attacks against a password. As always, effective social engineering
is a terrific nontechnical solution to “forgotten” passwords.
Another generic search for password information, intext:(password | passcode |
pass) intext:(username | userid | user), combines common words for passwords and
user IDs into one query.This query returns a lot of results, but the vast majority
of the top hits refer to pages that list forgotten password information, including
either links or contact information. Using Google’s translate feature, found at
http://translate.google.com/translate_t, we could also create multilingual password
searches.Table 9.3 lists common translations for the word password
English Translations of the Word Password
Language Word Translation
German password Kennwort
Spanish password contraseña
French password mot de passe
Italian password parola d’accesso
Portuguese password senha
Dutch password Paswoord
NOTE
The terms username and userid in most languages translate to username
and userid, respectively.
Searching for Credit Card Numbers,
Social Security Numbers, and More
Most people have heard news stories about Web hackers making off with customer
credit card information.With so many fly-by night retailers popping up
on the Internet, it’s no wonder that credit card fraud is so prolific.These momand-
pop retailers are not the only ones successfully compromised by hackers.
Corporate giants by the hundreds have had financial database compromises over
the years, victims of sometimes very technical, highly focused attackers. What
might surprise you is that it doesn’t take a rocket scientist to uncover live credit
card numbers on the Internet, thanks to search engines like Google. Everything
from credit information to banking data or supersensitive classified government
documents can be found on the Web. Consider the (highly edited) Web page
This document, found using Google, lists hundreds and hundreds of credit
card numbers (including expiration date and card validation numbers) as well as
the owners’ names, addresses, and phone numbers.This particular document also
included phone card (calling card) numbers. Notice the scroll bar on the righthand
side of Figure 9.9, an indicator that the displayed page is only a small part
of this huge document—like many other documents of its kind. In most cases,
pages that contain these numbers are not “leaked” from online retailers or ecommerce
sites but rather are most likely the fruits of a scam known as phishing,
in which users are solicited via telephone or e-mail for personal information.
Several Web sites, including MillerSmiles.co.uk, document these scams and
hoaxes. Figure 9.10 shows a screen shot of a popular eBay phishing scam that
encourages users to update their eBay profile information.
Once a user fills out this form, all the information is sent via e-mail to the
attacker, who can use it for just about anything.
Tools and Traps
Catching Online Scammers
In some cases, you might be able to use Google to help nab the bad guys.
Phishing scams are effective because the fake page looks like an official
page. To create an official-looking page, the bad guys must have examples
to work from, meaning that they must have visited a few legitimate companies’
Web sites. If the fishing scam was created using text from several
companies’ existing pages, you can key in on specific phrases from the fake
page, creating Google queries designed to round up the servers that hosted
some of the original content. Once you’ve located the servers that contained
the pilfered text, you can work with the companies involved to
extract correlating connection data from their log files. If the scammer visited
each company’s Web page, collecting bits of realistic text, his IP should
appear in each of the log files. Auditors at SensePost (www.sensepost.com)
have successfully used this technique to nab online scam artists.
Unfortunately, if the scammer uses an exact copy of a page from only one
company, this task becomes much more difficult to accomplish.
Social Security Numbers
Social Security numbers (SSNs) and other sensitive data can be easily located
with Google as well as via the same techniques used to locate credit card numbers.
For a variety of reasons, SSNs might appear online—for example, educational
facilities are notorious for using an SSN as a student ID, then posting
grades to a public Web site with the “student ID” displayed next to the grade.A
creative attacker can do quite a bit with just an SSN, but in many cases it helps
to also have a name associated with that SSN. Again, educational facilities have
been found exposing this information via Excel spreadsheets listing student’s
names, grades, and SSNs, despite the fact that the student ID number is often
used to help protect the privacy of the student! Although we don’t feel it’s right
to go into the details of how this data is located, several media outlets have irresponsibly
posted the details online. Although the blame lies with the sites that are
leaking this information, in our opinion it’s still not right to draw attention to
how exactly the information can be located.
Personal Financial Data
In some cases, phishing scams are responsible for publicizing personal information;
in other cases, hackers attacking online retails are to blame for this breach of
privacy. Sadly, there are many instances where an individual is personally responsible
for his own lack of privacy. Such is the case with personal financial information.
With the explosion of personal computers in today’s society, users have
literally hundreds of personal finance programs to choose from. Many of these
programs create data files with specific file extensions that can be searched with
Google. It’s hard to imagine why anyone would post personal financial information
to a public Web site (which subsequently gets crawled by Google), but it
must happen quite a bit, judging by the number of hits for program files generated
by Quicken and Microsoft Money, for example. Although it would be
somewhat irresponsible to provide queries here that would unearth personal
financial data, it’s important to understand the types of data that could potentially
be uncovered by an attacker.To that end,Table 9.4 shows file extensions for various
financial, accounting, and tax return programs. Ensure that these filetypes
aren’t listed on a webserver you’re charged with protecting.
File Extension Description
afm Abassis Finance Manager
ab4 Accounting and Business File
mmw AceMoney File
Iqd AmeriCalc Mutual Fund Tax Report
et2 Electronic Tax Return Security File (Australia)
tax Intuit TurboTax Tax Return
t98-t04 Kiplinger Tax Cut File (extension based on two-digit return
year)
mny Microsoft Money 2004 Money Data Files
mbf Microsoft Money Backup Files
inv MSN Money Investor File
ptdb Peachtree Accounting Database
qbb QuickBooks Backup Files reveal financial data
qdf Quicken personal finance data
soa Sage MAS 90 accounting software
sdb Simply Accounting
stx Simply Tax Form
tmd Time and Expense Tracking
tls Timeless Time & Expense
fec U.S. Federal Campaign Expense Submission
wow Wings Accounting File
Searching for Other Juicy Info
As we’ve seen, Google can be used to locate all sorts of sensitive information. In
this section we take a look at some of the data that Google can find that’s harder
to categorize. From address books to chat log files and network vulnerability
reports, there’s no shortage of sensitive data online.Table 9.5 shows some queries
that can be used to uncover various types of sensitive data.
Query Description
intext:”Session Start AIM and IRC log files
* * * *:*:* *” filetype:log
filetype:blt blt +intext: AIM buddy lists
screenname
buddylist.blt AIM buddy lists
intitle:index.of cgiirc.config CGIIRC (Web-based IRC client) config file,
shows IRC servers and user credentials
inurl:cgiirc.config CGIIRC (Web-based IRC client) config file,
shows IRC servers and user credentials
“Index of” / “chat/logs” Chat logs
intitle:”Index Of” cookies.txt cookies.txt file reveals user information
“size”
“phone * * *” “address *” Curriculum vitae (resumes) reveal names
“e-mail” intitle:”curriculum vitae” and address information
ext:ini intext:env.ini Generic environment data
intitle:index.of inbox Generic mailbox files
“Running in Child mode” Gnutella client data and statistics
“:8080” “:3128” “:80” HTTP Proxy lists
filetype:txt
intitle:”Index of” ICQ chat logs
dbconvert.exe chats
“sets mode: +p” IRC private channel information
“sets mode: +s” IRC secret channel information
“Host Vulnerability Summary ISS vulnerability scanner reports, reveal
Report” potential vulnerabilities on hosts and
networks
“Network Vulnerability ISS vulnerability scanner reports, reveal
Assessment Report” potential vulnerabilities on hosts and networks
filetype:pot inurl:john.pot John the Ripper password cracker results
intitle:”Index Of” -inurl:maillog Maillog files reveals e-mail traffic
maillog size information
ext:mdb inurl:*.mdb inurl: Microsoft FrontPage database folders
Query Description
filetype:xls inurl:contact Microsoft Excel sheets containing contact
information.
intitle:index.of haccess.ctl Microsoft FrontPage equivalent(?)of htaccess
shows Web authentication info
ext:log “Software: Microsoft Microsoft Internet Information Services
Internet Information Services *.*” (IIS) log files
filetype:pst inurl:”outlook.pst” Microsoft Outlook e-mail and calendar
backup files
intitle:index.of mt-db-pass.cgi Movable Type default file
filetype:ctt ctt messenger MSN Messenger contact lists
“This file was generated Nessus vulnerability scanner reports, reveal
by Nessus” potential vulnerabilities on hosts and networks
inurl:”newsletter/admin/” Newsletter administration information
inurl:”newsletter/admin/” Newsletter administration information
intitle:”newsletter admin”
filetype:eml eml intext: Outlook Express e-mail files
”Subject” +From
intitle:index.of inbox dbx Outlook Express Mailbox files
intitle:index.of inbox dbx Outlook Express Mailbox files
filetype:mbx mbx intext:Subject Outlook v1–v4 or Eudora mailbox files
inurl:/public/?Cmd=contents Outlook Web Access public folders or
appointments
filetype:pdb pdb backup (Pilot Palm Pilot Hotsync database files
| Pluckerdb)
“This is a Shareaza Node” Shareaza client data and statistics
inurl:/_layouts/settings Sharepoint configuration information
inurl:ssl.conf filetype:conf SSL configuration files, reveal various configuration
information
site:edu admin grades Student grades
intitle:index.of mystuff.xml Trillian user Web links
inurl:forward filetype: UNIX mail forward files reveal e-mail
forward –cvs addresses
intitle:index.of dead.letter UNIX unfinished e-mails
Summary
Make no mistake—there’s sensitive data on the Web, and Google can find it.
There’s hardly any limit to the scope of information that can be located, if only
you can figure out the right query. From usernames to passwords, credit card and
Social Security numbers, and personal financial information, it’s all out there. As a
purveyor of the “dark arts,” you can relish in the stupidity of others, but as a professional
tasked with securing a customer’s site from this dangerous form of
information leakage, you could be overwhelmed by the sheer scale of your
defensive duties.
As droll as it might sound, a solid, enforced security policy is a great way to
keep sensitive data from leaking to the Web. If users understand the risks associated
with information leakage and understand the penalties that come with violating
policy, they will be more willing to cooperate in what should be a security
partnership.
In the meantime, it certainly doesn’t hurt to understand the tactics an adversary
might employ in attacking a Web server. One thing that should become
clear as you read this book is that any attacker has an overwhelming number of
files to go after. One way to prevent dangerous Web information leakage is by
denying requests for unknown file types. Whether your Web server normally
serves up CFM,ASP, PHP, or HTML, it’s infinitely easier to manage what should
be served by the Web server instead of focusing on what should not be served.
Adjust your servers or your border protection devices to allow only specific content
or file types.
Solutions Fast Track
Searching for Usernames
_ Usernames can be found in a variety of locations.
_ In some cases, digging through documents or e-mail directories might
be required.
_ A simple query such as “your username is” can be very effective in
locating usernames.
Searching for Passwords
_ Passwords can also be found in a variety locations.
_ A query such as “Your password” forgot can locate pages that provide a
forgotten-password recovery mechanism.
_ intext:(password | passcode | pass) intext:(username | userid | user) is
another generic search for locating password information.
Searching for Credit Cards
Numbers, Social Security Numbers, and More
_ Documents containing credit card and Social Security number
information do exist and are relatively prolific.
_ Some irresponsible news outlets have revealed functional queries that
locate this information.
_ There are relatively few examples of personal financial data online, but
there is a great deal of variety.
_ In most cases, specific file extensions can be searched for.
Searching for Other Juicy Info
_ From address books and chat log files to network vulnerability reports,
there’s no shortage of sensitive data online.
Monday, May 05, 2008 | 0 Comments
Google Talk Cheats
With Google Talk being all the craze right now, some people hating it, and others loving it, I figured that I would post a list of tips and tricks for those curious about the extra "features" Google implemented and has not said much about.
Registry Tweaks
You can edit most settings by opening regedit (start -> regedit),
and navigating to the key HKEY_CURRENT_USER\Software\Google\Google Talk.
The "Google/Google Talk" key has several sub-keys that hold different option values:
Accounts: This one has subkeys for each different account that has logged in on the client. These keys have different values that store the username, password and connection options.
Autoupdate: Stores the current version information. When the client checks for updates it compares Google's response with these values. If an update is needed, it will download and update the new version.
Options: This is the most interesting part, where most of the current hacks should be used (keep reading).
Process: Stores the process ID. Probably used by Google Talk to detect if it's already running or not.
1.) HKEY_CURRENT_USER\Software\Google\Google Talk\Options\show_pin
If 1, shows a "pin" next to the minimize button that keeps the windows on top of all the other open windows when clicked.
2.)HKEY_CURRENT_USER\Software\Google\Google Talk\Options\view_show_taskbutton
If 0, hides the taskbar button, and leaves the tray icon only, when the window is shown
3.)HKEY_CURRENT_USER\Software\Google\Google Talk\Options\away_inactive
If 1, status will be set as Away after the specified number of minutes.
4.)HKEY_CURRENT_USER\Software\Google\Google Talk\Options\away_screensaver
If 1, status will be set as Away after the specified number of minutes.
5.)HKEY_CURRENT_USER\Software\Google\Google Talk\Options\inactive_minutes
Number of inactive minutes to become away if auto-away is on.
More Tips & Tricks
Change the font size - While holding the control key, move the scroll wheel on your mouse either up or down. This trick works while being focused in either the read or write area.
Insert line breaks - If you want to have a message that spans multiple paragraphs, just hold shift and hit enter. You can add as many new lines as you want to create.
Bold Text - To write something bold, you can use an asterisk before and after the word, like *this* .
Italic Text - To use italics, use an underscore before an after the word, like _this_ .
Switch windows - Hitting tab will cycle through open windows. It will select minimized conversations, to expand them just hit enter. If you just want to cycle through IM's and don't care about the buddy list, control-tab will do that and will automatically expand a minimized conversation if you settle on one.
Invitation Tips - You don’t need to say Yes or No when someone wants to add you as a friend; you can simply ignore it, the request will go away. (On the other hand, someone with whom you chat often will automatically turn to be your friend, unless you disable this in the options). ]
Show Hyperlinks - You can show your homepage or blog URL simply by entering the it in your away message (at the top of the main window). It will automatically turn to a link visible to others.
A message can be 32767 characters long.
What you need to do to have conference calls: Open up a copy of Google Talk on all computers with which you wish to conference. After one copy is opened make a new shortcut for Google Talk but at the end of it add /nomutex. If you installed it to the default folder then your shortcut should read "C:\Program Files\Google\Google Talk\googletalk.exe" /nomutex. Open 2nd instances of the software on every user's computer. After this start a chain: User 1 should connect on one instance to user 2. User 2 will connect on his second instance to user 3. User 3 will connect using his second instance back to user 1. With this chain everyone is connected to everyone.How To
Conference Calls :
Nickname & Status Message :
Contacts :
You don't need to say Yes or No when someone wants to add you as a friend; you can simply ignore it, the request will go away. (On the other hand, someone with whom you chat often will automatically turn to be your friend, unless you disable this).
The Gmail account 'user@gmail.com' can't be invited as your friend.
Play Music :
It's possible to broadcast music, MP3, etc.. through Google Talk.
Unplug your microphone. Double click on the speaker icon in the lower right corner. This will open up "Volume Control". Select "Options" and then "Properties". Then check the button next to "Recording" then click OK. You may also have to change your setting under Mixer Device. Now the Recording Control screen should be up. On my computer I selected "Wave Out Mix". Click on the green phone in Google Talk and call your friend.
Ctrl + E - It centralizes the selected text, or the current line.Keyboard Shortcuts
Ctrl + R - It justifies to the right the selected text, or the current line.
Ctrl + L - It justifies to the left the selected text, or the current line.
Ctrl + I - The same thing does that Tab.
Tab - It is giving the area to each of the windows opened by Google Talk.
Ctrl + Tab - The same thing does that Shift + Tab .
Shift + Tab - The same thing does that Tab but in reverse.
Ctrl + Shift + L -Switch between points, numbers, letters, capital letters, roman numbers and capital roman numbers
Ctrl + 1 (KeyPad) - It does a simple space between the lines.
Ctrl + 2 (KeyPad) - It does a double space between the lines.
Ctrl + 5 (KeyPad) - A space does 1.5 between the lines.
Ctrl + 1 (NumPad) - It goes at the end of the last line.
Ctrl + 7 (NumPad) - It goes at the begin of the last line.
Ctrl + F4 - It closes the current window.
Alt + F4 - It closes the current window.
Alt + Esc - It Minimize all the windows.
Windows + ESC - Open Google Talk (if it's minimized, or in the tray)
F9 - Open Gmail to send an email to the current contact.
F11 - It initiates a telephonic call with your friend.
F12 - It cancels a telephonic call.
Esc - It closes the current window.
[HOWTO] Use multiple identities on Google Talk
Want to run Google Talk with multiple Gmail identities? If you have several Google Gmail accounts you also may want to run multiple instances of Google Talk This is especially important for families that share a single PC. Nothing worse than a family member signing you out so they can sign in under their own account!
Basically, to have "Google Polygamy" you need to run Google Talk with the following switch: /nomutex
Step 1: Right-click on the desktop
Step 2: Select New
Step 3: Select Shortcut
Step 4: Paste this into the text box:
"c:\program files\google\google talk\googletalk.exe" /nomutex
Step 5: Click Next and choose a shortcut name such as Google Talk1, Google Talk2, or something related to your Gmail account for easy remembering which account is which.
Step 6: Click OK a few times.
[HOWTO] Use Google Talk via a Web Browser
You want to use Google Talk anywhere ? Follow these guidelines :)
Step 1: Opens your favorite web browser at the following address :
http://www.webjabber.net:8080/jim/
Step 2: Follow the instructions of the Page.
Step 3: You can talk with your friends
Google's Secret Command-Line Parameters
There are a few secret parameters you can add to Google Talk and make it function differently.
The most important, I think, is /nomutex, which allows you to run more than one instance of GT. Here are the others:
/nomutex: allows you to open more than one instance of Google Talk
/autostart: when Google Talk is run with this parameter, it will check the registry settings to see if it needs to be started or not. If the "Start automatically with Windows" option is unchecked, it won't start.
/forcestart: same as /autostart, but forces it to start no matter what option was set.
/S upgrade: Used when upgrading Google Talk
/register: registers Google Talk in the registry, includig the GMail Compose method.
/checkupdate: check for newer versions
/plaintextauth: uses plain authentication mechanism instead then Google's GAIA mechanism. Used for testing the plain method on Google's servers.
/nogaiaauth: disables GAIA authentication method. The same as above.
/factoryreset: set settings back to default.
/gaiaserver servername.com: uses a different GAIA server to connect to Google Talk. Used for debug purposes only, there are no other known GAIA servers.
/mailto email@host.com: send an email with Gmail
/diag: start Google Talk in diagnostic mode
/log: probably has something to do with the diagnostic logging
/unregister: ?
/embedding: ?
To add these, open up your GT shortcut, and where it says "Target:" add one or more of these inside the quotations, but after the .exe part.
Command Line stuff
There are a few secret parameters you can add to Google Talk and make it function differently. The most important, I think, is /nomutex, which allows you to run more than one instance of GT. He Talk is run with this parameter, it will check the registry settings to see if it needs to be started or not. If the "Start automatically with Windows" option is unchecked, it won't start.
/forcestart: same as /autostart, but forces it to start no matter what option was set.
/S upgrade: Used when upgrading Google Talk
/register: registers Google Talk in the registry, includig the GMail Compose method.
/checkupdate: check for newer versions
/plaintextauth: uses plain authentication mechanism instead then Google's GAIA mechanism. Used for testing the plain method on Google's servers.
/nogaiaauth: disables GAIA authentication method. The same as above.
/factoryreset: set settings back to default.
/gaiaserver servername.com: uses a different GAIA server to connect to Google Talk. Used for debug purposes only, there are no other known GAIA servers.
/mailto email@host.com: send an email with Gmail
/diag: start Google Talk in diagnostic mode
/log: probably has something to do with the diagnostic logging
/unregister: ?
/embedding: ? To add these, open up your GT shortcut, and where it says "Target:" add one or more of these inside the quotations, but after the .exe part. ere are the others:
/autostart: when Google
Emotions :
All these emotions appears in color in a conversation : (but having them in an image would be better, like iChat or MSN)
:-|
:-O
:-x
:-P
:-D
;-)
:-(
:-)
B-)
:'(
:|
:O
:x
:P
:D
:)
:(
:)
**********************************************************************************
Misc Gtalk information
1. You don’t have to say YES or NO when someone adds you. Simply ignore it and the request will go away.
2. A message can be 32767 characters long.
3. You can change your Gtalk chat name in Account Page
4. Adding a web URL in custom message will result it to be clickable.
5.Gtalk supports these following emotions and they are in blue colors
:-| :-O :-x :-P :-D ;-) :-( :| :O :x :P :D :) :( ;-| ;-O ;-x ;-P ;-D ;-) ;-( ;| ;O ;x ;P ;D ;) ;( B-| B-O B-x B-P B-D B-) B-( B’( BO Bx BD B) B( B)
6.Gmail talk supports these following emotions and they are animated
:-| :=P :-D ;-):-( :P :D :) :( ;-) ;) B-)
More parameters for Gtalk Start -> Run
Here’s a complete list of what you can do with Gtalk in run command prompt.
"C:\Program Files\Google\Google Talk\googletalk.exe" /parameter
/nomutex: Open more than 1 Gtalk.
/autostart: Check the registry settings to see if Gtalk needs to be started. If the “Start automatically with Windows” option is unchecked, it won’t start.
/forcestart: Similar to /autostart, but forces Gtalk to start.
/S upgrade: Used when upgrading Google Talk
/register: registers Google Talk in the registry, includig the GMail Compose method.
/checkupdate: check for newer versions
/plaintextauth: uses plain authentication mechanism instead then Google’s GAIA mechanism. Used for testing the plain method on Google’s servers.
/nogaiaauth: disables GAIA authentication method. The same as above.
/factoryreset: set settings back to default.
/gaiaserver servername.com: uses a different GAIA server to connect to Google Talk. Used for debug purposes only, there are no other known GAIA servers.
/mailto email@host.com: send an email with Gmail
/diag: start Google Talk in diagnostic mode
/log: probably has something to do with the diagnostic logging
</p> <p>4. Adding a web URL in custom message will result it to be clickable.</p> <p>5.Gtalk supports these following emotions and they are in blue colors</p> <blockquote><p> :-| :-O :-x :-P :-D ;-) :-( :| :O :x :P :D :) :( ;-| ;-O ;-x ;-P ;-D ;-) ;-( ;| ;O ;x ;P ;D ;) ;( B-| B-O B-x B-P B-D B-) B-( B’( BO Bx BD B) B( B) </p></blockquote> <p>6.Gmail talk supports these following emotions and they are animated</p> <blockquote><p> :-| :=P :-D ;-):-( :P :D :) :( ;-) ;) B-) </p></blockquote> <p><strong><u>More parameters for Gtalk Start -> Run</u></strong><br> Here’s a complete list of what you can do with Gtalk in run command prompt.</p> <blockquote class="code"><p> "C:\Program Files\Google\Google Talk\googletalk.exe" <em>/parameter</em> </p></blockquote> <p><em>/nomutex</em>: Open more than 1 Gtalk.<br> <em>/autostart</em>: Check the registry settings to see if Gtalk needs to be started. If the “Start automatically with Windows” option is unchecked, it won’t start.<br> <em>/forcestart</em>: Similar to /autostart, but forces Gtalk to start.<br> <em>/S upgrade</em>: Used when upgrading Google Talk<br> <em>/register</em>: registers Google Talk in the registry, includig the GMail Compose method.<br> <em>/checkupdate</em>: check for newer versions<br> <em>/plaintextauth</em>: uses plain authentication mechanism instead then Google’s GAIA mechanism. Used for testing the plain method on Google’s servers.<br> <em>/nogaiaauth</em>: disables GAIA authentication method. The same as above.<br> <em>/factoryreset</em>: set settings back to default.<br> <em>/gaiaserver servername.com</em>: uses a different GAIA server to connect to Google Talk. Used for debug purposes only, there are no other known GAIA servers.<br> <em>/mailto email@host.com</em>: send an email with Gmail<br> <em>/diag</em>: start Google Talk in diagnostic mode<br> <em>/log</em>: probably has something to do with the diagnostic logging</p><br><br><h2>Rahul Dutt Avasthy</h2>i luv programmerworld<br><br>
Monday, May 05, 2008 | 0 Comments
IP Address Hack
In here I have figure out some very easy but cool ways to trace out the geographical location and various other infos like ISP details etc of a remote computer using its IP.
Well I guess its one of the most important must learn manul for boys out there if you want to impress your friends particularly gals whom you’ll meet online in a chat room and tell them their geographical locations and ISP details and make them surprised and impressed .
In the practical execution of this manual you don’t have to work much as it is very simple only you have to use your brain to understand some symbols and some format of expressions and use your IQ to execute things the right way.
What is IP and how to get the IP of a remote system::
Getting the IP or Internet Protocol of a remote system is the most important and the first step of hacking into it. Probably it is the first thing a hacker do to get info for researching on a system. Well IP is a unique number assigned to each computer on a network. It is this unique address which represents the system on the network. Generally the IP of a particular system changes each time you log on to the network by dialing to your ISP and it is assigned to you by your ISP. IP of a system which is always on the network remains generally the same. Generally those kind of systems are most likely to suffer a hacking attack because of its stable IP. Using IP you can even execute system commands on the victim’s computer.
Lets take the example of the following IP address: 202.144.49.110 Now the first part, the numbers before the first decimal i.e. 209 is the Network number or the Network Prefix.. This means that it identifies the number of the network in which the host is. The second part i.e. 144 is the Host Number that is it identifies the number of the host within the Network. This means that in the same Network, the network number is same. In order to provide flexibility in the size of the Network, here are different classes of IP addresses:
Address Class Dotted Decimal Notation Ranges
Class A ( /8 Prefixes) 1.xxx.xxx.xxx through 126.xxx.xxx.xxx
Class B ( /16 Prefixes) 128.0.xxx.xxx through 191.255.xxx.xxx
Class C ( /24 Prefixes) 192.0.0.xxx through 223.255.255.xxx
The various classes will be clearer after reading the next few lines.
Each Class A Network Address contains a 8 bit Network Prefix followed by a 24-bit host number. They are considered to be primitive. They are referred to as "/8''s" or just "8's" as they have an 8-bit Network prefix.
In a Class B Network Address there is a 16 bit Network Prefix followed by a 16-bit Host number. It is referred to as "16's".
A class C Network address contains a 24-bit Network Prefix and a 8 bit Host number. It is referred to as
"24's" and is commonly used by most ISP's.
Due to the growing size of the Internet the Network Administrators faced many problems. The Internet routing tables were beginning to grow and now the administrators had to request another network number from the Internet before a new network could be installed at their site. This is where sub-netting came in.
Now if your ISP is a big one and if it provides you with dynamic IP addresses then you will most probably see that whenever you log on to the net, your IP address will have the same first 24 bits and only the last 8 bits will keep changing. This is due to the fact that when sub-netting comes in then the IP Addresses structure becomes:
xxx.xxx.zzz.yyy
where the first 2 parts are Network Prefix numbers and the zzz is the Subnet number and the yyy is the host number. So you are always connected to the same Subnet within the same Network. As a result the first 3 parts will remain the same and only the last part i.e. yyy is variable.
***********************
For Example, if say an ISP xyz is given the IP: 203.98.12.xx Network address then you can be awarded any IP, whose first three fields are 203.98.12. Get it?
So, basically this means that each ISP has a particular range in which to allocate all its subscribers. Or in other words, all subscribers or all people connected to the internet using the same ISP, will have to be in this range. This in effect would mean that all people using the same ISP are likely to have the same first three fields of their IP Addresses.
This means that if you have done a lot of (By this I really mean a lot) of research, then you could figure out which ISP a person is using by simply looking at his IP. The ISP name could then be used to figure out the city and the country of the person. Right? Let me take an example to stress as to how cumbersome but easy (once the research is done) the above method can be.
In my country, say there are three main ISP’s:
ISP Name Network Address Allotted
ISP I 203.94.47.xx
ISP II 202.92.12.xx
ISP III 203.91.35.xx
Now, if I get to know the IP of an e-pal of mine, and it reads: 203.91.35.12, then I can pretty easily figure out that he uses ISP III to connect to the internet. Right? You might say that any idiot would be able to do this. Well, yes and no. You see, the above method of finding out the ISP of a person was successful only because we already had the ISP and Network Address Allotted list with us. So, what my point is, that the above method can be successful only after a lot of research and experimentation. And, I do think such research can be helpful sometimes.
Also, this would not work, if you take it all on in larger scale. What if the IP that you have belongs to someone living in a remote igloo in the North Pole? You could not possibly get the Network Addresses of all the ISP’s in the world, could you? If yes please send it to me J.
Well now I guess you have pretty good knowledge about what an IP is and what you can do by knowing the IP of a remote system. Now lets come to the point of finding out the IP of remote system.
Well you can easily figure out the IP of a remote system using the netstat utility available in the microsoft’s version of DOS. The netstat command shows the connections in which your system is engaged to and the ports they are using. Suppose you are checking your mail in hotmail and you want to find out the IP of msn. All you need to do is to open a dos window (command.com) and type netstat. You will see all the open connections of your system. There you will see something :
Proto Local Address Foreign Address State
TCP abhisek:1031 64.4.xx.xx:80 ESTABLISHED
Now you got the IP address of hotmail ass 64.4.xx.xx .
Similarly you can figure out the IP address of most http or ftp connections.
To know your own IP type the following command in a dos windows
C:\netstat –n
[this commands converts the IP name into IP addresses]
this is what you will probably see on typing the above command :
Proto Local Address Foreign Address State
TCP 203.xx.251.161:1031 194.1.129.227:21 ESTABLISHED
TCP 203.xx.251.161:1043 207.138.41.181:80 FIN_WAIT_2
TCP 203.xx.251.161:1053 203.94.243.71:110 TIME_WAIT
TCP 203.xx.251.161:1058 194.1.129.227:20 TIME_WAIT
TCP 203.xx.251.161:1069 203.94.243.71:110 TIME_WAIT
TCP 203.xx.251.161:1071 194.98.93.244:80 ESTABLISHED
TCP 203.xx.251.161:1078 203.94.243.71:110 TIME_WAIT
Here 203.xx.251.161 is your IP address.
Now lets clarify the format used by netstat :
Proto : It shows the type of protocol the connection with the remote system is using.
Here TCP (transmission control protocol) is the protocol used by my system to connect to other systems.
Local Address : It shows the local address ie the local IP. When the netstat command is executed without –n switch then the name of the local system is displayed and when the netstat is executed with –n switch then the IP of the local system is displayed. Here you can also find out the port used by the connection.
xxx.yyy.zzz.aaa:1024
in this format you will see the local address. Here 1024 is the port to which the remote system is connected in your system
Foreign Address :: It shows the IP address of the remote system to which your system is connected. In this case also if the netstat command is excuted with –n switch then you directly get the IP of the victim but if the netstat is executed without –n switch then you will get the address of the remote system. Something like
C:\netstat
Proto Local Address Foreign Address State
TCP abhisek:1031 msgr.lw4.gs681.hotmail.com:80 ESTABLISHED
Here msgr.lw4.gs681.hotmail.com is the address of the foreign system . putting this address in any IP lookup program and doing a whois lookup will reveal the IP of the remote system.
Note: The port to which your system is connected can be found from this in the same way as I have shown in the case of local address. The difference is that, this is the port of the remote system to which your computer is connected to.
Below I have produced a list of ports and popular services generally found to be running.
21 :: FTP port
80 :: http port
23 :: Telnet port
Note: If your execute the netstat command and find ports like 12345,27374 are open and are in use then make it sure that your sweat heart computer is infected with her boyfriend.. J J J J I mean your computer is infected with some sort of Trojan.
Below I have produced a list of commonly known Trojans and the ports they use by default. So if you find these ports open then get a good virus buster and get these stupid servers of the Trojans kicked out. Well if you want to play with these Trojan by keeping them in your computer but not letting them ruin your system performance then just disble it from the system registry run and they wont be loaded to memory each time when windows starts up[This trick doesn’t work for all Trojans].
Netbus :: 12345(TCP)
Subseven :: 27374(TCP)
Girl Friend :: 21554(TCP)
Back Oriface :: 31337 (UDP)
Well guys and gals I hope you are now well familiar with the term IP and what is the utility of IP in cyber world and how to get the IP of a remote system to which you are connected. I hope you find my writings very easy to undertstand. I know I lack the capacity of explaining myself but I try my level best to make things very easy and clear for you’ll.
How to get the IP of a remote system while chatting through msn messenger ::
This is a tutorial on how to get IP address from MSN messenger. This is actually
a really easy thing to do. It is not like going through the hard time and reversing
MSN messenger like many people think.
The IP address is only given when you accept or are sending a file through MSN
messenger. When you send IM's, the message is sent through the server thus hiding
your victims IP and your. But when you send a file or recieve a file, it is direct
connection between the two computers.
To obtain the IP accept a file transfer or send a file to the victim, when the file
sending is under way from the dos prompt type "netstat" without the quotation marks.
You should get a table like this:
Proto Local Address Foreign Address State
TCP kick:1033 msgr-ns29.msgr.hotmail.com:1863 ESTABLISHED
TCP kick:1040 msgr-sb36.msgr.hotmail.com:1863 ESTABLISHED
TCP kick:
The top name in the list is the server's address for IMing. There could be many of
the second name in the list, as a new connection is made to the server for every
room you are IMing to. You are looking for the address of the remote host in
this table it may be something similar to "host63-7-102-226.ppp.cal.vsnl.com" or “203..64.90.6”.
without the quotation marks.
All you need to do now is to put this address in you IP lookup programe and get the IP of the remote system.
Well 50%of the work is done now. Now you know how to get the IP of a remote system, so its time to trace it down and find some details about the IP.
Tracing an IP is quite simple. You can do it the easy way by using some sweet softwares like Visual Trace 6.0b
[ftp://ftp.visualware.com/pub/vr/vr.exe]
Neotrace
[http://www.neoworx.com/download/NTX325.exe]
or by our way ie. Using MS DOS or any other version of DOS.
Well I suggest you to use DOS and its tracert tool for tracing the IP cause using it will give you a clear conception about the art of tracing an IP and I guarantee that you will feel much satisfied on success than using a silly software. Furthur you will know how things work and how the IP is traced down and the different networks associated in this tracing process.
Let us take a look at tracert tool provided for DOS by Microsoft.
It is a very handy tool for peoples need to trace down an IP.
Just open any DOS windows and type tracert.
C:\windows>tracert
Usage: tracert [-d] [-h maximum_hops] [-j host-list] [-w timeout] target_name
Options:
-d Do not resolve addresses to hostnames.
-h maximum_hops Maximum number of hops to search for target.
-j host-list Loose source route along host-list.
-w timeout Wait timeout milliseconds for each reply.
You will now see a description of the tracert command and the switches associated with it.
Well these switches doesn’t makes much difference. All you can do is to increase the timeout in milliseconds by using –w switch if you are using a slow connection and the –d switch if you wish not resolve address to hostnames by default.
By default tracert performs a maximum of 30 hops trace. Using the –h switch you can specify the number of hops to perform.
Now its time for execution.
Let us trace down the IP yahoo.com [216.115.108.243]
TIP: If you have done a long research (I mean a lot) then simply looking at the IP you can figure out some info from it. For example the IP 203.90.68.8 indicates that the system is in India. In India IPs generally begin with 203 and 202
C:\WINDOWS>tracert yahoo.com
Tracing route to yahoo.com [216.115.108.243] over a maximum of 30 hops:
1 308 ms 142 ms 127 ms 203.94.246.35
2 140 ms 135 ms * 203.94.246.1
3 213 ms 134 ms 132 ms 203.94.255.33
4 134 ms 130 ms 129 ms 203.200.64.29
5 122 ms 135 ms 131 ms 203.200.87.75
6 141 ms 137 ms 121 ms 203.200.87.15
7 143 ms 170 ms 154 ms vsb-delhi-stm1.Bbone.vsnl.net.in [202.54.2.241]
8 565 ms 589 ms 568 ms if-7-0.bb8.NewYork.Teleglobe.net [207.45.198.65]
9 596 ms 584 ms 600 ms if-3-0.core2.NewYork.teleglobe.net [207.45.221.66]
10 * * * Request timed out.
11 703 ms 701 ms 719 ms if-3-0.core2.PaloAlto.Teleglobe.net [64.86.83.205]
12 694 ms 683 ms 681 ms if-6-1.core1.PaloAlto.Teleglobe.net [207.45.202.33]
13 656 ms 677 ms 700 ms ix-5-0.core1.PaloAlto.Teleglobe.net [207.45.196.90]
14 667 ms 673 ms 673 ms ge-1-3-0.msr1.pao.yahoo.com [216.115.100.150]
15 653 ms 673 ms 673 ms vl20.bas1.snv.yahoo.com [216.115.100.225]
16 666 ms 676 ms 674 ms yahoo.com [216.115.108.243]
Trace complete.
Note: Here I have traced yahoo.com. In place of yahoo.com you can give the IP of yahoo or any other IP you want to trace, the result will be the same.
Now carefully looking at the results you can figure out many information about yahoo’s server [216.115.108.243]
First packets of data leave my ISP which is at 203.94.246.35 .Similarly you can find out the different routers through which the packets of data are send and received to and from the target system. Now take a look at the 13th line you’ll see that the router is in PaloAlto.Teleglobe.net from this you can easily figure out that the router is in Palo Alto. Now finally look at the target system ie. Yahoo’s server vl20.bas1.snv.yahoo.com . Now you got the address of yahoo’s server. Now put this address in any IP lookup programe and perform and reverse DNS lookup and you will get most of the info about this address,like the place where it is in.
Well another thing you can find out using the tracert tool is that the number of hops (routers) the target system is away from you. In case of tracerouting yahoo.com we find that the target system ie yahoo’s server is 16 hops away from my system. This indicates that there are 16 routers between my system and yahoo’s server.
Apart from tracing an IP you can find out many usefull details about the target system using the tracert tool.
Firewall Detection
While tracerouting a target system, if you get * as an output then it indicates timeout error. Now if you peform another tracerout to the same taeget system at some other time with a good connection and in this way few times more and if you always get * as the output then take it for sure that the target system is running a firewall which prevents sending of data packets from the target system.
Example
Some days ago I tried to tracert hotmail’s server in plain and simple way using tracert without any trick.This is what I found out :
c:\windows>tracert 64.4.53.7
Tracing route to lc2.law5.hotmail.com [64.4.53.7]
over a maximum of 30 hops:
1 * * * Request timed out.
2 161 ms 147 ms 85 ms 203.90.69.81
3 126 ms 261 ms 219 ms 203.90.66.9
4 121 ms 115 ms 228 ms delswp2.hclinfinet.com [203.90.66.133]
5 727 ms 725 ms 711 ms 203-195-147-250.now-india.net.in [203.195.147.250]
6 1006 ms 794 ms 952 ms core-fae-0-0.now-india.net.in [203.195.147.3]
7 826 ms 731 ms 819 ms 213.232.106.9
8 885 ms 744 ms 930 ms 213.166.3.209
9 851 ms 1020 ms 1080 ms 213.232.64.54
10 1448 ms 765 ms 1114 ms pos8-0.core2.London1.Level3.net [212.113.0.118]
11 748 ms 789 ms 750 ms ge-4-2-1.mp2.London1.Level3.net [212.187.131.146]
12 719 ms 733 ms 846 ms so-3-0-0.mp1.London2.Level3.net [212.187.128.46]
13 775 ms 890 ms 829 ms so-1-0-0.mp2.Weehawken1.Level3.net [212.187.128.138]
14 853 ms 852 ms 823 ms so-3-0-0.mp1.SanJose1.Level3.net [64.159.1.129]
15 889 ms 816 ms 803 ms so-7-0-0.gar1.SanJose1.Level3.net [64.159.1.74]
16 * * * Request timed out.
17 * * * Request timed out.
18 * * * Request timed out.
19 * * * Request timed out.
20 * * * Request timed out.
21 * * * Request timed out.
22 * * * Request timed out.
23 * * * Request timed out.
24 * * * Request timed out.
25 * * * Request timed out.
26 * * * Request timed out.
27 * * * Request timed out.
28 * * * Request timed out.
29 * * * Request timed out.
30 * * * Request timed out.
Trace complete.
I performed the same tracert many times a day but concluded with the same result. This indicates that the systems after the router SanJose1.Level3.net has firewalls installed which prevents the outgoing of data packets.
Detecting Traceroute Attempts on your System
You can detect that an attacker is performing a traceroute on your system, if you see the following symptoms:
1. If you observe port scans on very high UDP ports. This symptom means that the attacker has performed a traceroute on your system. However, it could also mean a simply port scan. Either way, it signifies the fact that your system is being scanned.
2. If the packet-monitoring tool installed in your network, picks up several outgoing TTL-exceeding messages, then it is yet another sign that someone is doing a traceroute on your system.
3. If in these log files, you also observer an outgoing ICMP port unreachable error message, then it means that since a traceroute was done on your system and as the target system i.e. your system, was reached, it responded with this error message.
You can also find our more information on the attacker (if he performs a traceroute on your system) by simply studying the sniffer log files. If you observer the TTL values, then we can easily figure out the following information on the attacker by making use of OS detection techniques discussed earlier in this white paper:
The Operating System running on the attacker’s target system.
Number of hops away, the attacker is from you.
Easy Way:
The first way to change it is, if your NIC (Network Interface Card) supports cloning your MAC Address. If this is the case then you go to.
Start > Control Panel > Network Connections
Right Click on your NIC card and goto properties. Then click the button labeled Configure. It should bring up another form. Click on the advanced tab. You should see under Property "Locally Administered Address" or "Network Address". Click the radio button next to the text box, and type in your new MAC address. (note you do not use the "-" when you enter your no MAC Address.
To check and see if it worked or not go to
Start > Run > and type in "cmd"
When the terminal comes up issue the command.
ipconfig /all
-----------------------------------------------------------------------------------------------------------------------------------------------
Hard Way:
To change your MAC Address the hard way, you first go to
Start > Run > and type in "cmd"
Once the terminal comes up type in
"net config rdr"
It should bring up alot of things, but what you are worried about is
NetBT_Tcpip_{ The Numbers Between here}
Copy the numbers in between there and write it down somewhere, seeing that you will need them later.
After you are done with that go to
Start > Run > and type in "regedt32"
That should bring up the windows registry. Once the registry is up go to
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Class\{4D36E972-E325-11CE-BFC1-08002BE10318}
Click on the drop down menu and you should see the sub-categories
0000
0001
0002
and so on.
Click on each one and compare the "NetCfgInstanceId" Key with the number you wrote down earlier. Once you find a match double click on the key "NetworkAddress" and change the value to your new MAC address. Hit ok and reboot your system.
| There r several ways u can determine ur IP address information: IPCONFIG Start / Run / cmd IPCONFIG /ALL This opens a command window. One advantage is that u can send the information to a text file (IPCONFIG /ALL > c:\ip.txt) But sometimes the window shows show much information u need to scroll around to fine it. VIEW STATUS Control Panel / Network Connections / Double click the icons 4 ur network (If the network has an icon in the system tray u can also just double click on that icon) Click on the Support tab Click on the Details button ::::::::::::: Make Pictures Smaller Unavailable When u try nd send pictures through e-mail, u should normally be given the option to make them smaller. If this option is not available, a DLL file may need to be registered. Start Run regsvr32 shimgvw.dll ::::::::::::: Creating a Suspend Shortcut If u would like to create an icon to suspend ur computer, Right click on the Desktop New / Shortcut Enter in rundll32.exe PowrProf.dll, SetSuspendState Give it whatever name u want Now when u click on that shortcut, ur computer will shutdown nd suspend Submitted by Gabe ::::::::::::: Changing the User Type Normally in XP Pro, through the Control Panel / User Accounts icon, u r only allowed to create administrators or limited users. If u want to create Right click on My Computer Manage Local Users nd Groups Users Right click on the user u want to change Properties Member of tab Add button Advanced button Find Now button From here u see the full list of possibilities (e.g. Power User, Backup Operator etc.) ::::::::::::: | ||
| | some more Determining Which Services r Associated with SVCHOST Since so many critical services r run with each svchost, You can see which ones r being used by opening a cmd prompt nd running: tasklist /svc /fi "imagename eq svchost.exe" Note: This is available only with XP Pro ::::::::::::: Identify Faulty Device Drivers If u r having problems with lockups, blue screens, or can only get to safe mode, often the problem is due to a faulty device driver. One way to help identify them is through the use of the Verfier program Start / Run / Verifier Keep the default of Create Standard Settings Select the type of drivers u want to confirm A list of drivers to be verified on the next boot will be shown. Reboot If ur computer stops with a blue screen, u should get an error message with the problem driver To turn off the Verifier, run verifier /reset ::::::::::::: Viewing Installed Drivers If u want to see a list of installed drivers, u can run the driverquery program There r a lot of available switches to view different types of information. On use can be to export to a CSV file 4 viewing in Excel An example would then be: Driverquery /v /fo csv > drivers.csv |
Monday, May 05, 2008 | 0 Comments
Mobile Hackiing
A will not be held responsible in the event any criminal
charges be brought against any individuals misusing the
information in this Website to break the law......................................
Airtel Hack for free internet
these are all the tricks available !!
working too!It cannot go beyond this!!
This write up will explain to you how to speed up your Airtel Broadband connection / solve other problems regarding connection failures due to closed ports.
Although I use Airtel and a Beetel 220 BX modem as my basis for this write up, the same rules can be applied to others as well. So lets get started. First thing make sure your DSL modem is on. Fire up your browser. Type http://192.168.1.1 as the address with the following Username/Password - Username : admin Password : password Note : These are case sensitive. Make sure all are typed in lowercase. Click on Advanced Setup -> NAT in the page that loads. If you do not see these options try entering http://192.168.1.1/main.html as the address. Some routers/modems deliberately try to prevent users from accessing these options. On the NAT virtual servers page click the add button. Now add the port number that you wish to open up. You can even open up a range of ports using the add button. You should see something similar to the screenshot below. Click it to view full image
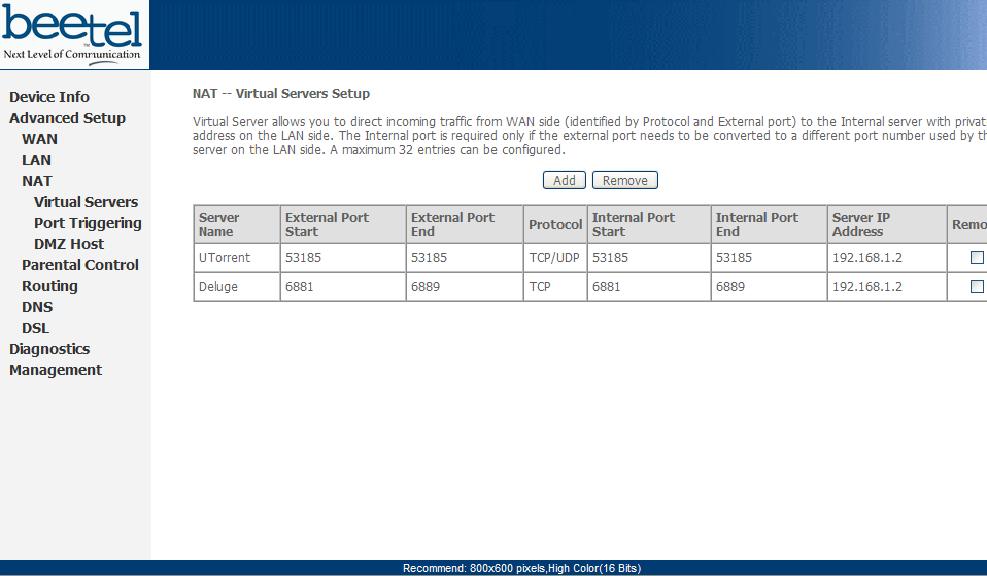 This technique can be used for any operating system / modem / service provider. It may vary slightly but the essential principle remains the same.
This technique can be used for any operating system / modem / service provider. It may vary slightly but the essential principle remains the same.
~cheers~
Serial/USB cable OR Infrared Device OR Bluetooth dongle
1) Activate Airtel Live! ( It’s FREE so no probs)
2) Create TWO Airtel gprs data accounts (yep TWO) and select the
FIRST as the active profile.
3) Connect your mobile to the PC (or Laptop) and install the driver for
your mobile’s modem.
4) Create a new dial-up connection using the NEW CONNECTION
WIZARD as follows
Connecting Device : Your mobile’s modem
ISP Name : Airtel (or anything you like)
Phone Number : *99***2# / Try 99***1
Username and Password : blank
5) Configure your browser and download manager to use the proxy
100.1.200.99 and port 8080.( My advice is to use Opera since you
can browse both wap and regular websites)
6) Connect to the dial-up account. You will be connected at 115.2
kbps (but remember, that is a bad joke).
7) Pick up your mobile and try to access any site. You will get “Access
Denied…”(except for Airtel Live!). IT DOES NOT MATTER.
Keep the mobile down.
8 ) On the PC ( or Laptop) open your browser, enter any address ,
press ENTER and…….WAIT
9) After a few seconds the page will start to load and you have the
WHOLE internet at your disposal. ***************************************************************************************************************
TWO
Under DATA COMM
~~~~~~~~~~~~
APN : airtelfun.com
USERNAME : blank
PASSWORD : blank
PASS REQ : OFF
ALLOW CALLS : AUTOMATIC
IPADDRESS :
DNSADDRESS :
DATA COMP : OFF
HEADER COMP : OFF
Under INTERNET PROFILES
~~~~~~~~~~~~~~~~
INTERNET MODE : HTTP or WAP (both worked for me)
USE PROXY : YES
IP ADDRESS : 100.1.200.99
PORT : 8080
USERNAME :
PASSWORD :
No Risk Here, Try it and Enjoy
Three
1st go to settings menu then to connectivity tab now choose the option Data comm. then "DATA ACCOUNTS" go to new account now the settings r as follows
ACCOUNT TYPE:GPRS
NEW ACCOUNT NAME:A1
APN:airtelfun.com
usr name: (blank)
password: (blank)
now save it
NOW!
go to Internet Setting in connectivity here choose intrnet profile--go to new profile setting are as below
NAME:A1
CONNECT USING:A1(which was created in data comm.)
save it
now u would be able to see it now selest it and take "more" option then select setting here in use proxy option it will be selected no if it is no then change it into yes
now go to proxy adress and give the adress as
100.1.200.99 and then the port number as 8080
Usr name:
password:
now save all the settings u made . come back 2 connectivity
choose streaming settings now in connect using option choose a1 that we created leave the use proxy option as no itself
THESE R THE SETTINGS
now access airtellive! from ur activated SE phone goto VIDEO GALLERY OR VIDEO UNLIMITED(varies according to states) choose live streaming then choose CNBC OR AAJTAK WHILE CONNECTING TO MEDIA SERVER cancel AFTER 9 or 10 sec then type any web adress if it shows access denied then once again select CNBC and wait for a few more sec than before if its fully connected also no prob its free then cancel it or if ur connected then stop it and the internet is ready to take of .GOOD LUCK SE AIRTEL USERS
alternate
For All Airtel Users
Requirements:
1. Airtel live (available 4 free)
2. Nokia series60 handset eg 6600,6630,n series,7610,6670 etc
3. Opera wap browser 4 mobile
Procedure:-
1. Go to ur connection settings and make a new internet profile using the default settings of airtel live. name that new profile as nething(for eg masala); change the home page of that profile to nething u like for eg www.google.com.
2. Go to ur Opera browser and set the default connection as AIRTEL LIVE. this is the original settings u received thru airtel.
3. Go to the services(in n6600) and Web(N6630) and change the default profile for connection as masala (newer one).
**Note: always make sure that ur access point is airtelfun.com
Apply:-
1. Open Opera and u will see that homepage of Airtel Live is opened. Minimize the application.
2. Now open web using the duplicate Profile and u will see that two gprs connections will work simultaneously and at the web or the services page it will show "Unable to connect" or any error. well thats the signal of ur success.
3. Simply go on the Opera with web on and open any site u want for free. No Charges No nothing.
U can also use it through ur computer..........
someone said dis too
The main principle behind this is we hav 2 fool the bsnl techies 2 activate portal and thus get gprs activated / get "G" signal on ur cell as bsnl portal (wap.cellone.in) needs "gprs signal on ur cel (whether gprs is formaly activated/registerd or not (by my method )i dont know)
NORMALLY THEY DONT DO THAT INSPITE OF THE FACT THAT THEY SHOULD ACTIVATE GPRS SIGNAL SERVICE FOR PORTAL!!!
AND THEY WILL GIVE U NO OF REASONS----
---THAT portal is message based , so go to cellone icon in menu and use that sms based portal (what the f**k)
---THAT portal service will be activated when u will activate gprs by filling up form and registering at nearest CCN!!
---THAT ur handset has some problems (if u say that "G" signal is not present)
----etc,etc!!
U HAVE 2 ACTIVATE PORTAL FIRST WHICH IS FREE AND U CAN EAT UP CC'S FOR THIS REASON!!
SO WHAT U HAV 2 DO IS--
1) SEND PORTAL to 3733 AND CONFIRMATION SHD COME WITH 5 MIN AT-MAXIMM !!
2) SEND FOR ATLEAST 20-30 TIMES (CAN B ANY MORE THAN THAT)
JUST S**K UP THE NETWORK(3733) WITH THESE MESSAGES !!!
THAT'S FREE NO!! BOTH ON POST AND PRE!!
3) NOW ALONG ALSO SEND 20-40 SMS AS GPRS TO 3733
(NO OF SMS DIRECTLY PROPORTIONAL 2 HATE FOR BSNL AND HOW EARLY U WNAN GET UR GPRS ACTIVATED) this is also free both on post and pre!!
4) U WILL GET CONFIRMATION IN BOTH CASES AND MSG TELLS U 2 GET SETTINGS FROM 9400024365, THE NO OF CC!!
HERE AT MY PLACE I CAN DIAL 9419024365 ALSO!
BOTH R TOLL FREE AND BOTH R LOCATED IN CHANDIGARH!!!
(((((((AND SOME OF THE CC'S SAY they cant give such sensitive information that where they r located, as if thay have a 3 rd world of their own! and the other dumbs said that they r in chandigarh!!!!)))))
I WOULD ADVISE ALL FIRST, 2 call them once 2 get the settings!!
(most of the times that is incorect but gives u an idea of settings in ur area))
Try and in ur 1 st call only,
talk roughly and tell them u r calling 10-20th time just for settings and is that their service!!!
5) Now when u get them save them AND plz post them here!!!
6) now GET ATLEAST 2-3 COMPLAINTS REGISTERED( each after 1 day) THAT UR PORTAL HAS NOT ACTIVATED AND GET THEIR SERIAL NO.
and in the end bombard them abt the status of all those complaints !!
b4 registering ur complaint they will hesitate much and always say taht they will b sendin new settings which r accurate! but dont belive them and just register complaints!!
6)AFTER THAT, u have 2 only wait until "G" signal is there on ur screen!!
LOOK, WHAT I HAVE WRIITEN ABV IS METHOD by which i got activated my "G" service !!! without fillin any form or such and without any money drain!!
may be since it bypasses the formal way of registeration, that is why this trick is working !!!!!!!!!!!!
U may also Try this
first open ur msg window and type LIVE and send it to 2567 so that after 5 min u get the setting of Airtel Live or if u have already no need for this procedure.
now then open that setting and copy all the settings from it and create one access point manually which has all the settings like Airtel Live has.
now only one change will be there and it would be in access point name which is "Airtelmms.com" instead of originally "Airtelgprs.com".
ok u've done it just active that setting and access free airtel gprs on ur phone.
Another Trick
somya_cseYou need a PC or a Laptop and the required connectivity tools ,ie.,
Serial/USB cable OR Infrared Device OR Bluetooth dongle
1) Activate Airtel Live! ( It’s FREE so no probs)
2) Create TWO Airtel gprs data accounts (yep TWO) and select the
FIRST as the active profile.
3) Connect your mobile to the PC (or Laptop) and install the driver for
your mobile’s modem.
4) Create a new dial-up connection using the NEW CONNECTION
WIZARD as follows
Connecting Device : Your mobile’s modem
ISP Name : Airtel (or anything you like)
Phone Number : *99***2#
Username and Password : blank
5) Configure your browser and download manager to use the proxy
100.1.200.99 and port 8080.( My advice is to use Opera since you
can browse both wap and regular websites)
6) Connect to the dial-up account. You will be connected at 115.2
kbps (but remember, that is a bad joke).
7) Pick up your mobile and try to access any site. You will get “Access
Denied…”(except for Airtel Live!). IT DOES NOT MATTER.
Keep the mobile down.
8 ) On the PC ( or Laptop) open your browser, enter any address ,
press ENTER and…….WAIT
9) After a few seconds the page will start to load
main thing is the advance initialization command.
a recent comment says dat
Guys i tried and its working, I'm using airtel chennai,..the Method TWO worked, also i request everyone to change the Phone number from *99***2 to *99***1 and its working,.. it'll get connected at 462.8kbps but its the speed between the phone and your computer but actual BAndwidth is 42kbps
BSNL hack for Internet
Free gprs in bsnl
here are the steps to perform:-
Logic: the server has a major bug in it, by which it fails to block two simultaneous connections from the phone and establishes a connection with full internet working,
Supported devices: all phones with multichannel gprs support
For connection on your mobile phone:-
1) Make two connections like bsnlportal and BSNLPORTAL1
(names of profile don’t matter, u can keep one as billgates and shahrukhkhan lol..the basic purpose of names is to enable the user to differentiate between the two accounts,)
2) Select the application you got to have the full connection working on.
Surpassingly “web” now just select “bsnlportal” profile and select a link like wap.cellone.in the page will get open, just press the red button such that the “web” application goes in the background.
Make sure that the gprs connection is still established with the web app. Two parallel lines on the top left of the screen will confirm this
3) Now open any other app that requires web connection like opera. Select BSNLPORTAL and open any other link like wap.google.com, u will get error –
the aim of using the other app is to perform multi-channel gprs,
this is verified by seeing some dots on the pre-existing connection established by “web”
(step 2)
“Access denied.
Technical description:
403 Forbidden - You are not allowed to communicate with the requested resource.”
4) close opera and open web and open a site like esato.com
5) if everything is done as said here then esato will load and voila! We have the whole internet!
For connection on pc.
1)create a connection and enter the number to be dialed as *99***1#
2) enter the following string as extra initialization command
3)now dial from pc, the connection will be established
4)pick the phone and open “web” open “wap.cellone.in” the phone shows error .
5) close “web” and then from the browser open www.google.com
and voila! The whole intenet is here
settings for profiles
apn: celloneportal
ip: 192.168.51.163
port : 8080
leave other fields blank as they are of the least concern!
the browser settings on pc too go the same as mentioned above!
Mixed Bag (Good)
Mobile Secret Codes
Nokia 31xx
____________
Firmware version
*#0000# or *#3110#
IMEI Code
*# 06 #
Restores Factory Settings
*#7780#
Warranty Codes
*#92702689# (= *#war0anty#)
Just scroll down through the information. If entering the above code requires a
further warranty code try entering the following:
6232 (OK) : Month and year of manufacture
7332 (OK) : Last repair date
7832 (OK) : Purchase date (if previously set)
9268 (OK) : Serial number
37832 (OK) : Set purchase date (this can only be done once)
87267 (OK) : Confirm transfer
Nokia 5110
_____________
IMEI Number *#06#
For checking the IMEI (International Mobile Equipment Identity).
---------------------------------------------------------
Security Code 12345
Default security code is 12345. If you forgot your security code, there s so many program on the net which allowed you to know the security code likes Security ID Generator, Nokia IMEI Changer, etc.
update:
Security ID Generator (SID.EXE) and IMEI Generator (NOKIAIMEI.EXE) doesn t works with Nokia 5110
Resetting Security Code
If you accidentally lock the phone or forgot the security code, the best thing to do is check it with your local Nokia dealer. For advanced user, you can use WinTesla, PCLocals or LogoManager program to read the security code or resetting the code (You will need an FBUS/MBUS (or compatible) cable to do this.
---------------------------------------------------------
Software Version *#0000#
For checking the phones software (SW) - called firmware revision information.
e.q : Version V. 4.51 (26-03-98) will display
V 04.51
26-03-98
NSE-1
first line:
The Software Version (my guess is that this software has been used in previously Nokia-phones, what do you say?!).
second line:
The Date of the SW release.
third line:
NHE-8 has something to do with the type of phone you are dealing with. Is it GSM 900 (standard), GSM 1800 (DCS1800) or GSM 1900 (PCS1900)?
Nokia 2110, 3110, 8110(i) are all NHE types. The only thing that vary is the code after NHE- ("8").
NHE = GSM 900, NHK =GSM 1800 - The number in the end = the model (2110i = 4 etc.)
The 5110 and 6110 is called NSE-1 and NSE-3...this may be because it supports EFR (?)
update:
Newest Software Version was V5.22 (xx-xx-99)
V 05.22
01-07-99
NSE-1
If your software version is V4.00, upgrade your software version to latest version. V4.00 contains bugs that sometimes will show message,
"SIM Card Not Ready" even the card is already inside the phone.
---------------------------------------------------------
Software Update
The only thing to do (for you and me) is for us to go to the nearest Nokia dealer and make him do it for you. Just remember that it is supposed to be free (a receipt is required) so don t let him tell you anything else!
---------------------------------------------------------
SIM clock *#746025625# [*#sim0clock#]
to check if the Sim-Clock can be Stopped. This option is depen on your service provider network. (Sim-clock-stop is a kind of standby mode which will save battery time)
update:
This code doesn t work on phone with software version 4.59.
---------------------------------------------------------
Waranty Code *#92702689# [*#war0anty#]
Menu:
Displays Serial Number.
Displays the Month and Year of Manufacture (0698)
Displays (if there) the date where the phone was purchased (MMYY) you can here set the Purchasing Date
(Warning: You can only do this once - so be careful what you write)
Displays the date of the last repairment - if found (0000)
The next screen has Transfer User Data? (the same option as the 8110)
To exit turn the phone off and then back on.
---------------------------------------------------------
SP Lock The Service provider (SP) lock
Is used to lock the cell phone to the SP s SIM card. Once the cell phone is locked to a specific operator, if one inserts a SIM card from a different operator the phone will refuse to accept it!
The cell phone will however accept another SIM card from the same operator.
All Nokia phones (2110 and newer) have four different SIM locks which can be used to lock the phone for up to 4 different providers. But most phones with restriction only have one lock activated. ( lock 1)
The main code used in Nokia phones is:
#pw+(master code)+Y#
This code is able to check, activate or remove Sim card restriction (SP-lock).
Use the * key to get the p, + and w chars.
Y has to be 1,2,3 or 4 - depending of what lock you what to deal with.
#pw+1234567890+1# for Provider-Lock status
#pw+1234567890+2# for Network-Lock status
#pw+1234567890+3# for Provider(???)-Lock status
#pw+1234567890+4# for SimCard-Lock status
(master code) is a 10 digit code, based on the phones IMEI number.
(I can NOT give you the master code SO DON T ASK ME FOR IT! )
Please click here to learn more about how to obtain mastercode and find out the lock status of your phone
eq. To remove restriction on lock 1 type following code:
#pw+(master code)+1#
If you just want to check your phone use 10 random numbers Eg. 1234567890 as the (master code)
eq. To check if phone if restricted on lock 1 type the following code:
#pw+1234567890+1#
Please NOTE that these codes could be used with care!
A user told me that it s only possible to type in about 3 different codes on each lock! Then something bad will happen ..therefore be careful!
---------------------------------------------------------
How can I check what locks have my phone closed?
There is 2 methods:
Use winlock to see the state of the locks, pressing Read Info.The Counter is the number of times that you have tried unlock your phone using an incorrect master code.
You can check it entering an imaginary mastercode on your phone but, it s not recommended because if you try enter a code 5 times your phone will not work anymore. By example, if you press at your phone #pw+1234567890+2# (note that # , p , w and + characters must be selected from * key) and your phone give you Code Error then your phone have lock 2 closed, if you get the message SIM Restriction Off your phone have lock 2 opened.
Look the table above to see how can check all locks:
Lock number Description Sequence to Check
1 Provider Lock #pw+1234567890+1#
2 Network-Lock #pw+1234567890+2#
3 Another Provider Lock #pw+1234567890+3#
4 SIM Card Lock #pw+1234567890+4#
---------------------------------------------------------
Unlock SP-Lock
Here is a way to Unlock your phone which is Service Provider locked, without to know SPLock code. With a Nokia 16xx/21xx/31xx/51xx/81xx that are SIMlocked to one privider you can bypass the SP lock like this:
First of all, PIN CODE MUST BE ON, then press:
C
C and hold until it clears display
* and hold until start to blink
* and hold until start to blink
04***your pin>#
Each time you turn your phone OFF it resets the lock, so this need to be done each time you ll turn your phone ON
The phone now says: PIN CODE CHANGED (or ACCEPTED)
and the SIM card is accepted until you restart the phone again.
NOTE: On vesion 5.04 Nokia has removed this option !
update:
There s another Nokia service provider lock generator for DOS (somehere on the net) called 5161un.zip (for Nokia 51xx-61xx models) This program uses the #pw+(master code)+1# code to unlock the phone. With this software you need to have a access to the eeprom..
---------------------------------------------------------
Bypass the SP-lock
With a Nokia 16xx/21xx/31xx/51xx/81xx that are SIM locked to one privider you can bypass the SP lock like this:
Insert sim card of diferent provider.
Turn on the phone and press the UP VOLUME key for 3 sec. then release it and the phone says PIN CODE ?
Press the "C" key.
Then Press * and wait until it desapear and apear again, then press * one more time and 04*PIN*PIN*PIN#
The phone now says: PIN CODE CHANGED (or ACCEPTED)
and the SIM card is accepted until you restart the phone again.
update:
On version 5.04 Nokia has removed this option !
---------------------------------------------------------
How to open lock 1 and 4?
You will need Winlock software and MBUS cable to do this. Winlock is a Nokia service program that you can use to open lock 1 and 4, really you are closing locks when you do that, but when you write ????? at MCC+MNC and MSIN text box, the phone don t understand it and consider that it s open.
That trick only works for lock 1 and 4, but not for lock 2 and 3. If you did not know your lock type, please read our miscellaneous tips page first. or read at above section in this page.
Install winlock 1.10
Connect your MBUS nokia data cable
Run Winlock
Push Read Phone, if you have Lock 2 or Lock 3 closed you can not open your phone, but you can try change Lock 2.
Select State Close in Lock 1 and Lock 4, fill out MCC+MNC and MSIN text boxes with ??????? and Push Close Locks.
Now you can use any operator card in your phone. If you get any error when you do that do the following steps:
Select State Automatic in Lock 1 and Lock 4 and change type to User in Lock 1 and Lock 4, fill out MCC+MNC and MSIN text boxes with ?????????? and Push Close Locks.
Select State Automatic in Lock 1 and Lock 4 and change type to Factory in Lock 1 and Lock 4, fill out MCC+MNC and MSIN text boxes with ?????????? and Push Close Locks.
If you continue getting errors you must turn off your phone and reset computer and try again.
---------------------------------------------------------
How to open lock 2?
When operators companies close lock2 you can only use the contract or prepaid card for this operator, but you can use another operator company prepaid card if you know what GID1 must write.
Install Winlock
Run Winlock
Configure Winlock. Select menu Winlock->Defaults and change GID byte count to 2.
Push Read Phone, and write down GID1 info that appear in lock 2.
Insert the prepaid card from a different operator company.
We must find out a the GID1 info adecuate for our new prepaid or contract card, take a look at our GID1 list and check if your operator and SIM card type is included, if not try to get a phone that have lock 2 closed and have the SIM card type that you want to use in your phone, and read GID1 info with winlock. You can try to write the most used GID1 codes like 0000,10FF,01FF, or FFFF, etc.
Change Lock 2 Type from User To Factory or from Factory to User.
Push Close Locks
Your phone will be reset every time you push Close Locks, if your card is not acepted the GID1 is not correct, repeat from step 4 until you find the correct GID1.
If you get error you must turn off your phone and reset computer and try again.
If you want your phone accept your original prepaid card write in GID1 the code you read at step 2 and close locks.
Exist a GID1 list?
In addition to the official way to open locks that Nokia service centers use with TDB4 or TDF-4(for WinTesla) security boxes, there is two secrets methods:
Opening the phone and adding a chip inside phone motherboard. But you will loose any warranty of your phone.
Using a special software with a MBUS Nokia cable. I don t have this software. Please don t bother me asking me about that. The only thing i know about that is that a friend is removing lock 2 using a special software. He don t make this for money, only for fun.
--------------------------------------------------------
Main Code #pw+(master code)+Y#
This code is able to check, activate or remove Sim card restriction (SP-lock).
Use the * key to get the p, + and w chars.
Y has to be 1,2,3 or 4 - depending of what lock you what to deal with.
#pw+1234567890+1# for Provider-Lock status
#pw+1234567890+2# for Network-Lock status
#pw+1234567890+3# for Provider(???)-Lock status
#pw+1234567890+4# for SimCard-Lock status
(master code) is a 10 digit code, based on the phones IMEI number.
update:
I get report that told me the code didn t works for Optimus Card
---------------------------------------------------------
Enhanced Full Rate Codec (EFR)
Enhanced Full Rate will give you much better sound quality when you enable it. The new Enhanced Full Rate CODEC adopted by GSM uses the ASELP (AlgebraicCode Excitation Linear Prediction) compression technology. This technology allows for much great voice quality in the same number of bits as the older Full Rate CODEC. The older technology was called LPC-RPE (Linear Prediction Coding with Regular Pulse Excitation). Both operate at 13 kilobits.(but you take up more space on the network, so they can charge you more)
*3370# and EFR will be activated after a reboot of the phone ( consumes more power )
#3370#
and EFR will be switched off after a reboot of the phone.
---------------------------------------------------------
Half Rate Codec (HR)
Half Rate will give you bad sound quality, which gives the service provider the opportunity to have more calls on the network; and you might get a lower charge from them. (Will give you 30% longer talk-time)
*4720# Half Rate coded will be activated after a reboot of the phone ( better standby time )
#4720# Half Rate coded will be de-activated after a reboot of the phone
---------------------------------------------------------
Unblocking Code
Unblock PIN1 : **05*PUK*newPIN1*newPIN1#@
UnBlock PIN2 : **052*PUK2*newPIN2*newPIN2#@
---------------------------------------------------------
Hiding your phone number
Dial 141 then the number you want to call eg. 141#######
This should stop your number been sent to the caller. (*)
(*) This only works on UK phones, if anybody has tried this and works, please let me know.
---------------------------------------------------------
Unlocking PIN2 for software version
V 05.07
20.11.98
NSE-1
If your SimCard is locked by your SP, you can check it and if it is, you will get the "wrong code" message on the display (for use 1234567890)
If your SimCard is locked by your SP, you can t unlock PIN2 !
---------------------------------------------------------
Blocking phone number at Cantel AT&T
If you have one of those cantel at&t phones if you press #0000# you can block your number
at no extra charge.
---------------------------------------------------------
New Menu on Emergency Calls *3001#12345#
Brings a new menu that gives you access to the emergency calls ( 911 Etc. ). It will give you FREE calls! (only the ones you put in the emergency!! )
This option will depend on your GSM operator
---------------------------------------------------------
Your number in your display
Goto menu 3-7 Call cost settings.
Turn ON the Call costs limit 3-7-1. PIN2 code Required.
Put in the limit with the phone number.
eg. my phone # is 019 2184697
Enter the limit as 2184697
Goto menu 3-7-2 Show costs in. PIN2 code Required.
Select Currency.
Enter Unit price : 1
Enter Currency name as 019 (per my phone # eg. above)
Now the phone number 019 2184697 will remains on the 4th row of the display.
Secondly, if you press the # key, it prompt which line to be used; Line 1 or 2.
---------------------------------------------------------
Free Call Tip
The tips needs Net Monitor enabled. Be aware that the trick will remove Netmonitor in some sw versions like v4.73 and v5.04.
Launch the Net Monitor in your Nokia 51xx / 61xx
Execute the test number 497
Free calling for about 90 sec should now have been activated.
---------------------------------------------------------
Nokia 5110 PIN-Out
Pin-Outs: Bottom view, keyboard up, counting from the left
V V 1 2 3 4 5 6 V
(o) | | [= = = = = =] | |
7 8 9 10 11 12
1 - VIN CHARGER INPUT VOLTAGE 8.4V 0.8A
2 - CHRG CTRL CHARGER CONTROL PWM 32Khz
3 - XMIC MIC INPUT 60mV - 1V
4 - SGND SIGNAL GROUND
5 - XEAR EAR OUTPUT 80mV - 1V
6 - MBUS 9600 B/S
7 - FBUS_RX 9.6 - 230.4 KB/S
8 - FBUS_TX 9.6 - 230.4 KB/S
9 - L_GND CHARGER / LOGIC GND
Nokia 61xx
__________
Firmware version
*#0000# or *#61x0#
IMEI Code
* # 06 #
Warranty Codes
*#92702689# (= *#war0anty#)
Just scroll down through the information. If entering the above code requires a
further warranty code try entering the following:
6232 (OK) : Month and year of manufacture
7332 (OK) : Last repair date
7832 (OK) : Purchase date (if previously set)
9268 (OK) : Serial number
37832 (OK) : Set purchase date (this can only be done once)
87267 (OK) : Confirm transfer
Enhanced Full Rate (EFR) and Half Rate Mode (HFR)
*3370# to activate Enhanced Full Rate - Makes calls sound better, but
decreases the battery life by about 5%.(I recommend this one)
#3370# to deactivate Enhanced Full Rate
*4720# to activate Half Rate Mode - Drops call quality, but increases battery
life by about 30%.
#4720# to deactivate Half Rate Mode
Nokia 81xx
_____________
Show IMEI code
* # 06 #
Software Version
* # 8110 #
This code shows you software version, date of manufacture and hardware number of your phone.
Warranty Codes
*#92702689# (= *#war0anty#)
Just scroll down through the information. If entering the above code requires a
further warranty code try entering the following:
6232 (OK) : Month and year of manufacture
7332 (OK) : Last repair date
7832 (OK) : Purchase date (if previously set)
9268 (OK) : Serial number
37832 (OK) : Set purchase date (this can only be done once)
87267 (OK) : Confirm transfer
Sim Clock information
To check if the Sim-Clock can be stopped type: *#746025625# (= *#sim0clock#)
Nokia 8810
____________
Firmware version
*#0000# or *#8810#
IMEI Code
* # 06 #
Warranty Codes
*#92702689# (= *#war0anty#)
Just scroll down through the information. If entering the above code requires a
further warranty code try entering the following:
6232 (OK) : Month and year of manufacture
7332 (OK) : Last repair date
7832 (OK) : Purchase date (if previously set)
9268 (OK) : Serial number
37832 (OK) : Set purchase date (this can only be done once)
87267 (OK) : Confirm transfer
Enhanced Full Rate (EFR) and Half Rate Mode (HFR)
*3370# to activate Enhanced Full Rate - Makes calls sound better, but
decreases the battery life by about 5%.(I recommend this one)
#3370# to deactivate Enhanced Full Rate
*4720# to activate Half Rate Mode - Drops call quality, but increases battery
life by about 30%.
#4720# to deactivate Half Rate Mode
Mobile Cheat Stuff
NOKIA
1 Imagine ur cell battery is very low, u r expecting an important call and u don't have a charger.
Nokia instrument comes with a reserve battery. To activate, key is "*3370#"
Ur cell will restart with this reserve and ur instrument will show a 50% incerase in battery.
This reserve will get charged when u charge ur cell next time.
*3370# Activate Enhanced Full Rate Codec (EFR)-Your phone uses the best sound quality but talk time is reduced by approx. 5%
#3370# Deactivate Enhanced Full Rate Codec( EFR)
*#4720# Activate Half Rate Codec - Your phone uses a lower quality sound
but you should gain approx 30% more Talk Time
*#4720# Deactivate Half Rate Codec
2 *#0000# Displays your phones software version,
1st Line :S oftware Version,
2nd Line : Software Release Date,
3rd Line : Compression Type
3 *#9999# Phones software v ersion if *#0000# does not work
4 *#06# For checking the International Mobile Equipment Identity (IMEI Number)
5 #pw+1234567890+1# Provider Lock Status. (use the "*" button to obtain the "p,w" and "+" symbols)
6 #pw+1234567890+2# Network Lock Status. (use the "*" button to obtain the "p,w" and "+" symbols)
7 #pw+1234567890+3# Country Lock Status. (use the "*" button to obtain the "p,w" and "+" symbols)
8 #pw+1234567890+4# SIM Card Lock Status.(use the "*" button to obtain the "p,w" and "+" symbols)
9 *#147# (vodafone) this lets you know who called you last *#1471# Last call (Only vodofone)
10 *#21# Allows you to check the number that "All Calls" are diverted To
11 *#2640# Displays security code in use
12 *#30# Lets you see the private number
13 *#43# Allows you to check the "Call Waiting" status of your phone.
14 *#61# Allows you to check the number that "On No Reply" calls are diverted to
15 *#62# Allows you to check the number that "Divert If Unrea chable(no service)" calls are diverted to
16 *#67# Allows you to check the number that "On Busy Calls" are diverted to
17 *#67705646#R emoves operator logo on 3310 & 3330
18 *#73# Reset phone timers and game scores
19 *#746025625# Displays the SIM Clock status, if your phone supports this power saving feature "SIM Clock Stop Allowed", it
means you will get the best standby time possible
20 *#7760# Manufactures code
21 *#7780# Restore factory settings
22 *#8110# Software version for the nokia 8110
23 *#92702689# (to rember *#WAR0ANTY#)
Displays -
1.Serial Number,
2.Date Made
3.Purchase Date,
4.Date of last repair (0000 for no repairs),
5.Transfer User Data.
To exit this mode -you need to switch your phone off then on again
24 *#94870345123456789# Deactivate the PWM-Mem
25 **21*number# Turn on "All Calls" diverting to the phone number entered
26 **61*number# Turn on "No Reply" diverting to the phone number entered
27 **67*number# Turn on "On Busy" diverting to the phone number entered
Each command is prefixed with either one or two * or # characters as follows:
** Register and Activate
* Activate
## De-Register (and Deactivate)
# Deactivate
*# Check Status
© Call button
Once each command has been entered, if it is a network command (as opposed to a local handset command) it must be transmitted to the network by pressing the YES (receiver) key which acts as an enter key - this is represented here with the © character. Always enter numbers in full international format +CountryAreaNumber ( e.g. +447712345678).
Command Description Command String
Security
Change call barring code **03*OldCode*NewCode*NewCode#©
Change call barring code **03*330*OldCode*NewCode*NewCode#©
Change PIN code **04*OldPIN*NewPIN*NewPIN#©
Change PIN2 code **042*OldPIN2*NewPIN2*NewPIN2#©
Unlock PIN code (when PIN is entered wrong 3 times) **05*PUK*NewPIN*NewPIN#©
Unlock PIN2 code (when PIN2 is entered wrong 3 times) **052*PUK2*NewPIN2*NewPIN2#©
Display IMEI *#06#
Call Forwarding (Diversions)
De-register all call diversions ##002#©
Set all configured call diversions to number and activate **004*number#©
De-register all configured call diversions (no answer, not reachable, busy) ##004#©
Unconditionally divert all calls to number and activate **21*number#©
Activate unconditionally divert all calls *21#©
De-register unconditionally divert all calls ##21#©
Deactivate unconditionally divert all calls #21#©
Check status of unconditionally divert all calls *#21#©
Divert on no answer to number and activate **61*number#©
Activate divert on no answer *61#©
De-register divert on no answer ##61#©
Deactivate divert on no answer #61#©
Check status of divert on no answer *#61#©
Divert on not reachable to number and activate **62*number#©
Activate divert on not reachable *62#©
De-register divert on not reachable ##62#©
Deactivate divert on not reachable #62#©
Check status of divert on not reachable *#62#©
Divert on busy to number and activate /td> **67*number#©<
Activate divert on busy *67#©
De-register divert on busy ##67#©
Deactivate divert on busy #67#©
Check status of divert on busy *#67#©
Change number of seconds of ringing for the given service before diverting a call (such as on no answer). Seconds must be a value from 5 to 30. De-registering the same divert will also delete this change! **service*number**seconds#© (Service numbers, see below)
Call barring
Activate barr all outgoing calls (see Security to set code) **33*code#©
Deactivate barr all outgoing calls #33*code#©
Check status of barr all outgoing calls *#33#©
Activate barr all calls **330*code#©
Deactivate barr all calls #330*code#©
Check status of barr all calls /td> *#330*code#©<
Activate barr all outgoing international calls **331*code#©
Deactivate barr all outgoing international calls #331*code#©
Check status of barr all outgoing international calls *#331#©
Activate barr all outgoing international calls except to home country **332*code#©
Deactivate barr all outgoing international calls except to home country #332*code#©
Check status of barr all outgoing international calls except to home country *#332#©
Activate barr all outgoing calls **333*code#©
Deactivate barr all outgoing calls #333*code#©
Check status of barr all outgoing calls *#333#©
Activate barr all incoming calls **35*code#©
Deactivate barr all incoming calls #35*code#©
Check status of barr all incoming calls *#35#©
Activate barr all incoming calls when roaming **351*code#©
Deactivate barr all incoming calls when roaming #351*code#©
Check status of barr all incoming calls when roaming *#351#©
Activate barr all incoming calls **353*code#©
Deactivate barr all incoming calls #353*code#©
Check status of barr all incoming calls *#353#©
Call waiting
Activate call waiting *43*#©
Deactivate call waiting #43##©
Check status of call waiting *#43#©
Calling Line Identification
The following only works if CLIP and CLIR are enabled (ask your service provider)
CLIP: Presentation of the number of the incoming call
Activate CLIP **30#©
Deactivate CLIP ##30#©
Check status of CLIP *#30#©
CLIR: Presentation of one's own number to the to the called party
Activate CLIR **31#©
Activate CLIR for the actual call *31#number©
Deactivate CLIR ##31#©
Deactivate CLIR for the actual call #31#number©
Check status of CLIR *#31#©
COLP: Presentation of the actual number reached (if number called was diverted to another number
Activate COLP *76#©
Deactivate COLP #76#©
Check status of COLP *#76#©
COLR: Presentation of the original number called by the calling party (if the call was diverted to this cellphone)
Activate COLR *77#©
Deactivate COLR #77#©
Check status of COLR *#77#©
Nokia Service Mannuals hacked
Nokia 6210 :
Monday, May 05, 2008 | 0 Comments


